F5 Firewall Solutions > 2. Advanced Multi-Layer Firewall Protection > 2.3. Module 3: AFM Protocol Inspection IPS Source | Edit on
2.3.2. Lab 2: Protocol Inspection - Compliance Checks¶
Estimated completion time: Thirty Five 35 minutes
Compliance Checks model protocols and applications and flag deviations from the model. End users can’t add compliance checks, but some of them have parameters the user can modify. We’ll look at a couple of these checks and modify one. Have fun!
2.3.2.1. Task 1: The Inspection Profile¶
You will create an Inspection Profile containing compliance checks.
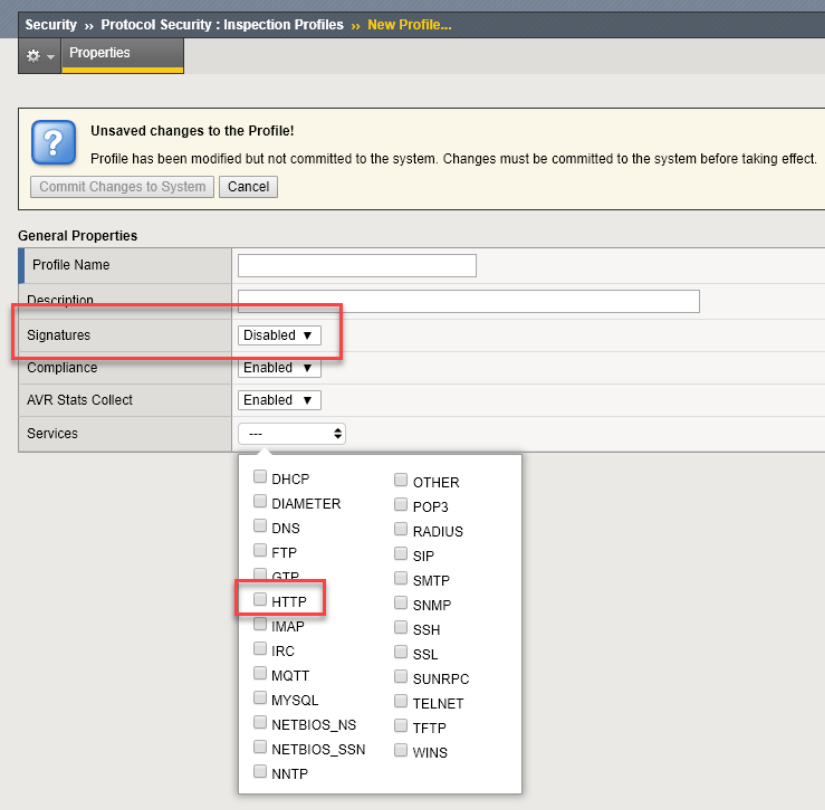
- Navigate to Security > Protocol Security > Inspection Profiles and click ‘Add’, select ‘New’
- Name the profile ‘my-inspection-profile’
- Disable Signatures
- Make sure Compliance is enabled.
- Under Services, Select HTTP.
Note
You have to wait a few seconds after selecting HTTP
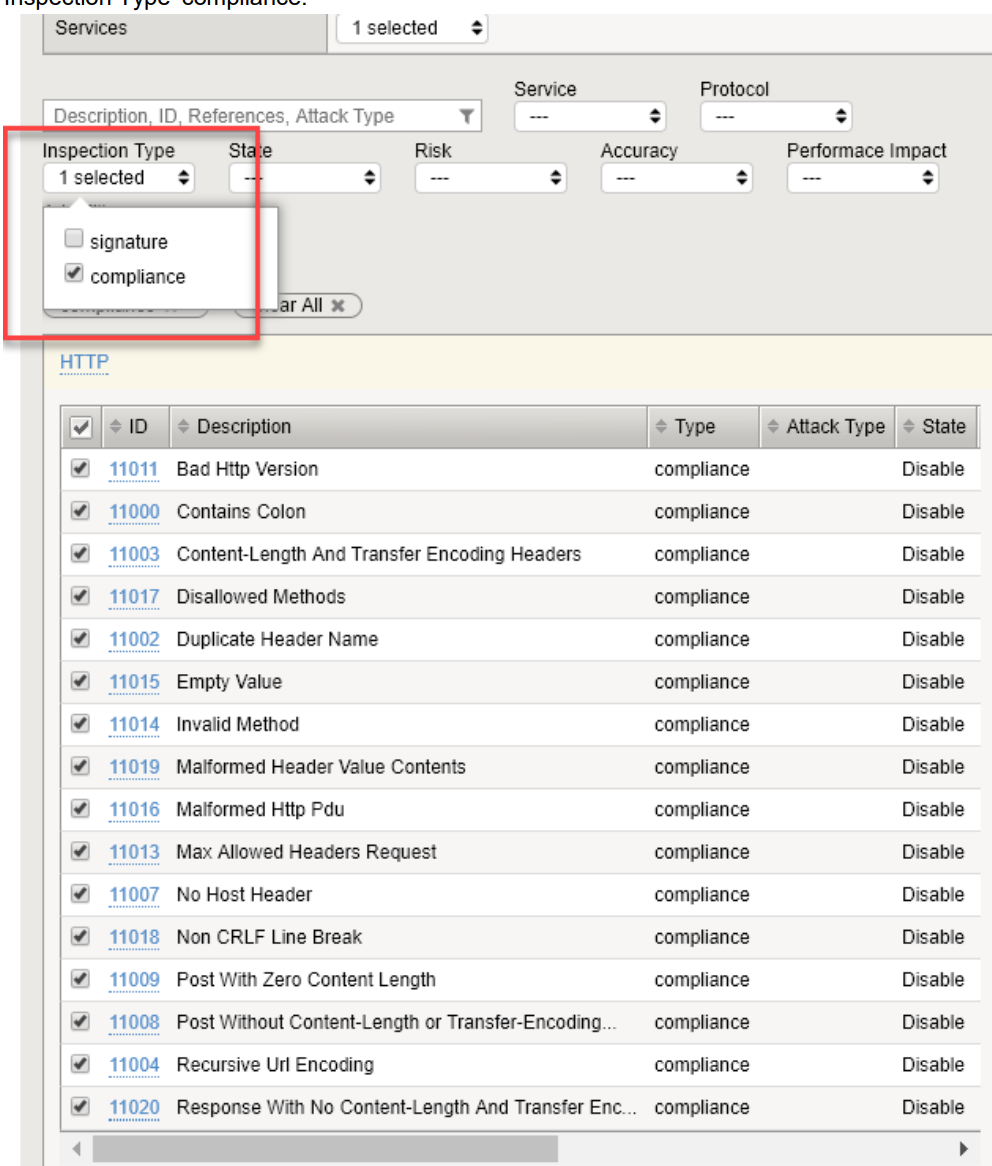
- When the HTTP Service appears, click to open the Inspection list for HTTP, and select Inspection Type ‘compliance.’
- Click the checkbox to select all the HTTP compliance checks.
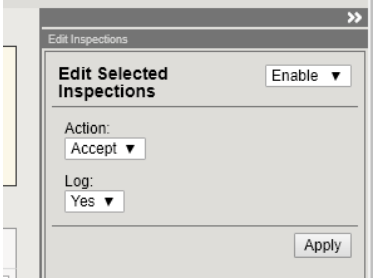
- In the edit window in the upper-right of the F5 GUI, make the following selections:
- Enable the selected inspections
- Set the ‘Action’ to ‘Accept’
- Enable logging
Note
These should be the default actions, so they most likely are already set for you.
- Click ‘Apply’
- Click ‘Commit Changes to System’
You should now have an Inspection Policy.
2.3.2.2. Task 2: Apply the Profile to the Global Policy¶
- Navigate to Security > Network Firewall > Active Rules
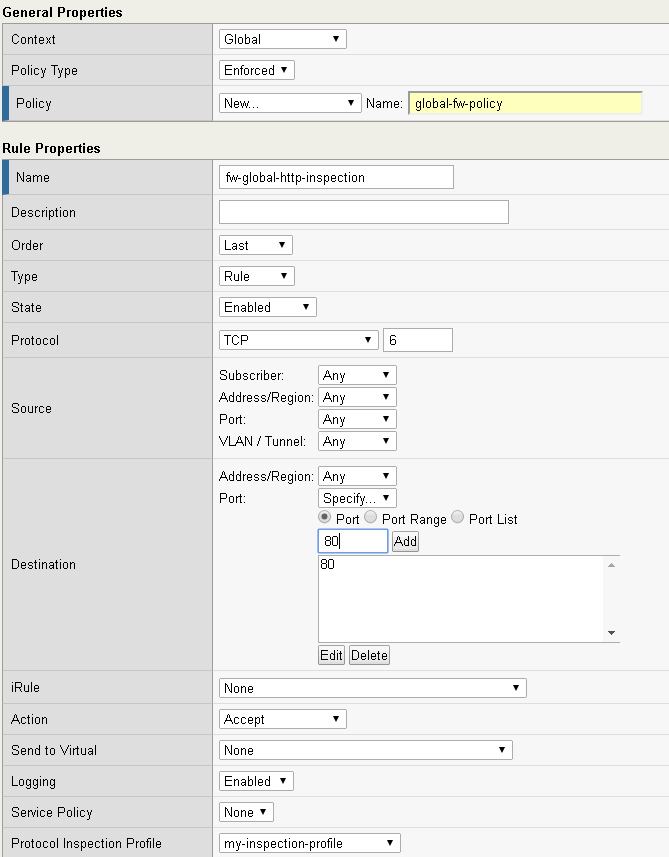
- Change Context to ‘Global’
- Click ‘Add Rule’
- Make a new policy named ‘global-fw-policy’
- Make a new rule named fw-global-http-inspection’
- Configure the new rule:
- Protocol ‘TCP’
- Set the Destination port to 80
- Action ‘Accept’
- Protocol Inspection Profile: ‘my-inspection-profile’
- Enable logging
- Click Save
2.3.2.3. Task 2.5: Create testing Virtual server on port 80¶
To get an understanding of how the IPS function works, we need the manual commands we can issue via Telnet. Because Telnet does not work very well with SSL, we need to create a virtual server on port 80 instead of the one on 443 that we have been using so far. Remember this is only for testing, and the IPS functionality can work perfectly well on encrypted traffic ( as long as we terminate the SSL )
- Check if the pool “pool_www.mysite.com” exists. Does it already exist? Only if it does not exist, please create it as follows:
| Name | Health Monitor | Members | Service Port |
|---|---|---|---|
| pool_www.mysite.com | tcp_half_open | 10.10.121.129 | 80 |
- Create a virtual server with no HTTP profile. Use the following settings, leave everything else default.
| Parameter | Value |
|---|---|
| name | IPS_VS |
| IP Address | 10.10.99.40 |
| Service Port | 80 |
| SNAT | automap |
| Pool | pool_www.mysite.com |
Note
Note that we neither applied an Inspection Policy to this VS, nor did you apply a Firewall Policy to this VS. And yet, the IPS is now functional on this VS. Can you think why this is? This is because the global firewall policy is in affect, and the Inspection Policy will be invoked by the Global Firewall Policy.
2.3.2.4. Task 3: Test the Inspection Profile¶
- From the Cygwin session, or from the DOS prompt, enter this command:
telnet 10.10.99.40 80
The expected output is:
Trying 10.10.99.40...
Connected to 10.10.99.40
Escape character is '^]'.
Enter the following ( Suggestion: copy and paste ):
GET /index.html HTTP/5
(hit Enter key two times)
The expected HTTP response is:
HTTP/1.1 200 OK
( and lots more HTTP headers, etc.)
- Check the results.
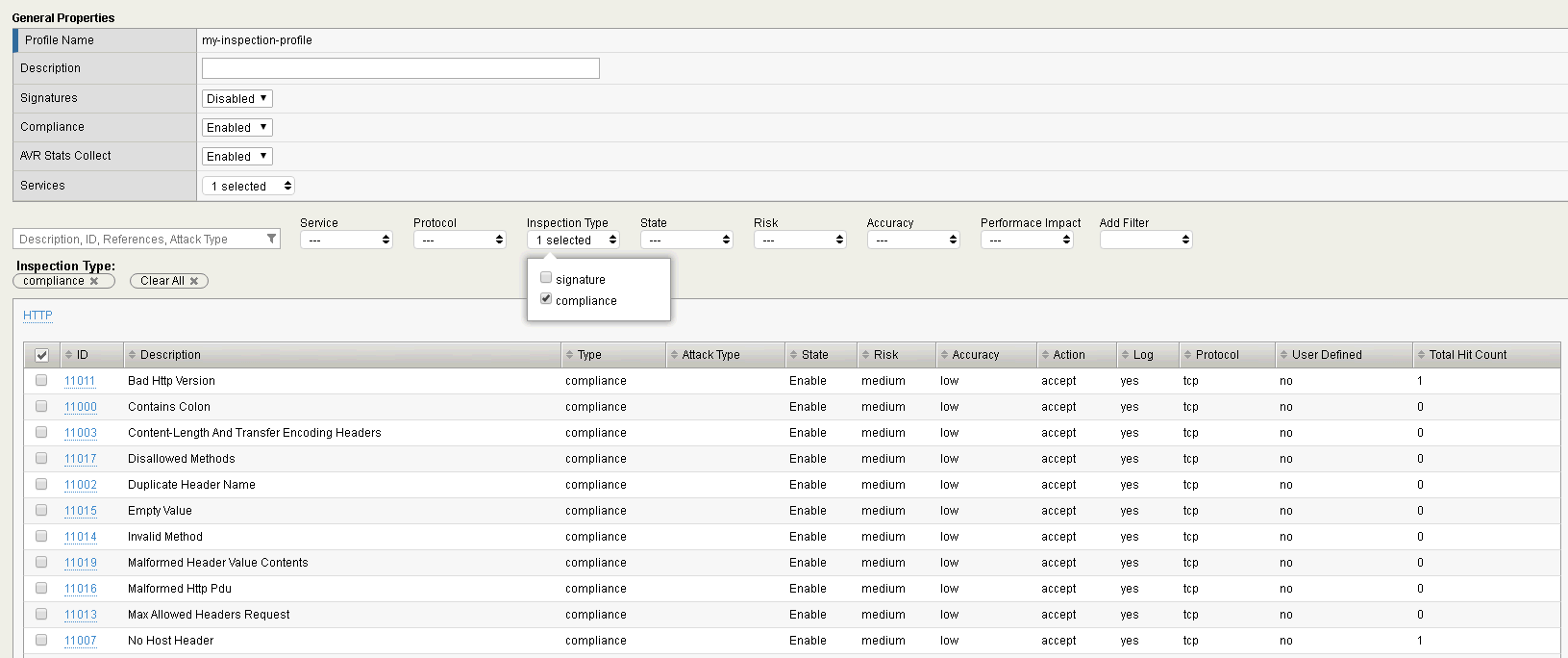
- Navigate to Security > Protocol Security > Inspection Profiles > my-inspectionprofile
- Filter for Inspection Type ‘compliance’
- Look at the Total Hit Count for HTTP Compliance Check ID 11011 “Bad HTTP Version.” We expect to see a hit count of at least 1, and a missing host header count of at least 1.
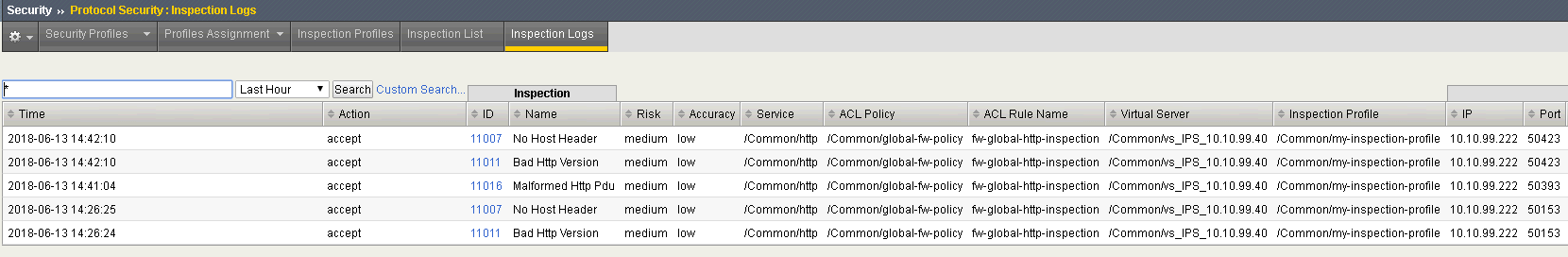
- Look at the protocol inspection logs. Go to Security > Protocol Security > Inspection Logs. You can see the incoming ip address and port, among other things.
2.3.2.5. Task 4: Modify a Compliance Check¶
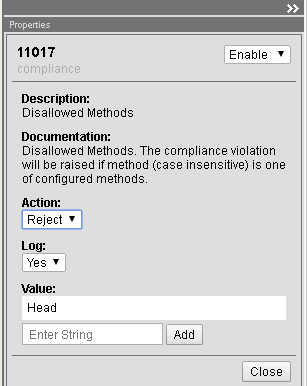
- Select Compliance Check 11017 ‘Disallowed Methods’
- Enter the value “Head” and click ‘Add’
- Click ‘Commit Changes to System’
2.3.2.6. Task 5: Test the Modified Compliance Check¶
- From the Cygwin session, enter (or copy and paste) this command:
telnet 10.10.99.40 80
The expected output is:
Trying 10.10.99.40...
Connected to 10.10.99.40
Escape character is '^]'.
Enter the following ( Suggestion: copy and paste ):
HEAD /index.html HTTP/1.1
Expected output:
HTTP/1.1 400 Bad Request
- Check the results.
Note
Just an interesting point to make again, this is the IPS code checking HTTP, not the HTTP Profile ( This VS does not have an HTTP Profile )
- Navigate to Security > Protocol Security > Inspection Profiles > my-inspection-profile
- Filter for Inspection Type ‘compliance’
- Look at the Total Hit Count for HTTP Compliance Check ID 11017 “Disallowed Methods.” You may have to refresh the page.
- We expect to see a hit count of 1.
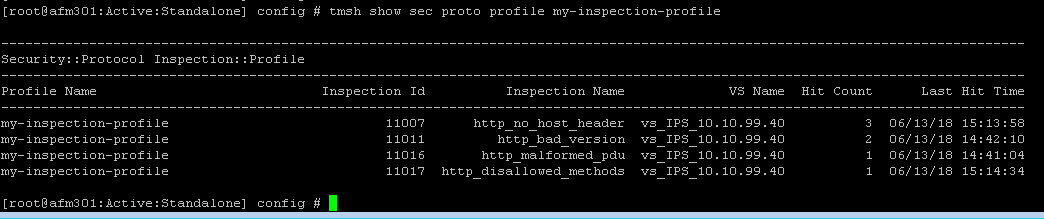
- Look at the stats. Enter the following command on the Big-IP command line:
tmsh show sec proto profile my-inspection-profile
We expect to see a Hit Count of at least 1 (more if you’ve done it multiple times).
Note
This completes Module 4 - Lab 2